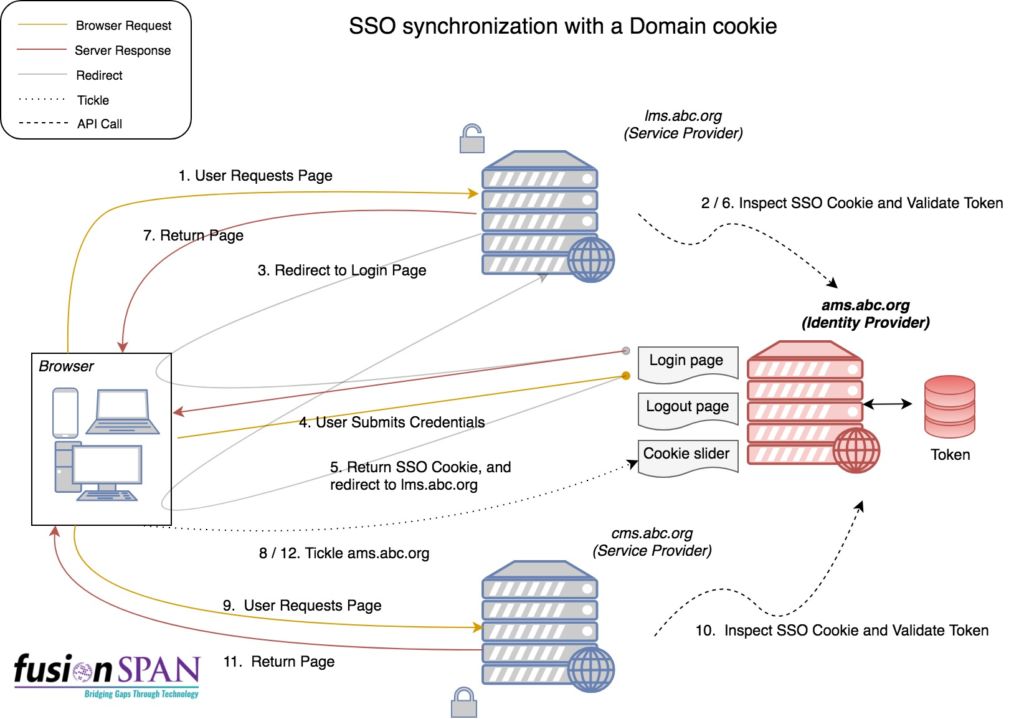
There are a number of different implementations for Single Sign-On (SSO). SSO is generally approached in one of two ways – The first is a browser-side implementation which usually involves an integration that redirects the user to an Identity Provider’s login page (Identity Provider is the website that is the system of record in which the user accounts reside), while the second is a back-end integration that consumes an Identity Provider’s web services (API) to authenticate users.

The usefulness of most SSO implementations tends to end at the moment of authentication. This is sufficient when all is needed is to allow users to authenticate and validate the user’s authorization. Unfortunately, for organizations that own and manage multiple websites, the challenge beyond authentication lies with “synchronizing” the login sessions of all of the websites, and maintaining a seamless user experience which would ideally look something like this:
- Single Sign-On: When the user Logs In to any of the websites, then whenever she/he navigates or is redirected to one of the other websites, she/he is automatically logged in.
- Single Sign-Out: When the user Logs Out of “any” of the websites, she/he is unable to access restricted content on any of the other websites. In essence, the user is Logged out from the other websites as well.
- Session Expiration: Whenever the Identity Provider’s session “Expires,” the user should not be able to access restricted content on the other Service Provider websites.
- When a user’s session on a Service Provider website expires, it is automatically restarted if the Identity provider’s authenticated session is still active.